Here’s a discomfiting thought: Experts say that even if you create a solid password with numerals and special characters, it can be cracked in eight...
The 7 Key Categories of Threat Actors
In cybersecurity, the term “threat actor” might refer to lone agents, organized criminal groups, or entire entities seeking to impact your personal security or that...
4 Things Your Home Office Needs
Whether you’re a longtime work-at-home veteran or a COVID newbie, here are some key elements of a secure home office...
Starbucks Safety: Security Tips for Public Computing
Millions of workers, cooped up at home for nearly a year, are taking every opportunity to escape the house. Take a couple precautions with you...
Data Security: Myth vs. Reality
In today’s world it seems people read and hear only what they already believe—even when it comes to security. How else to explain all the...
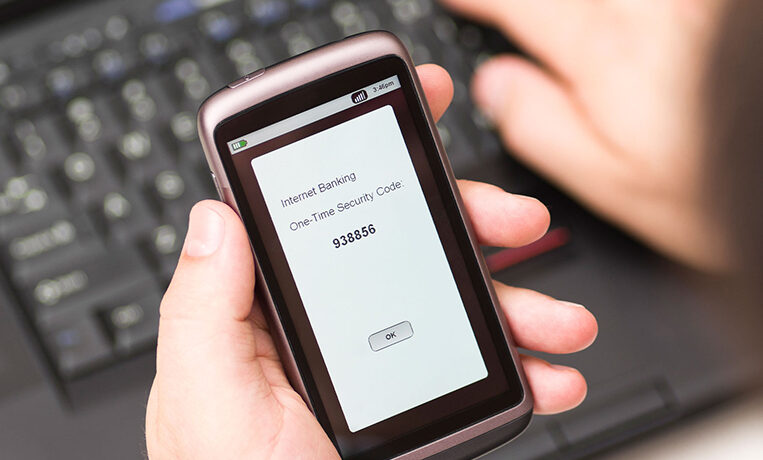
2FA: 6 Places to Start
These days, most people have at least some familiarity with two-factor authentication (2FA). For example, your ATM card uses 2FA. Here are 6 other places...
Are You Keeping Your CISO Up At Night?
You probably don't think about it too much. Why would you? You have your own job to worry about. But there are a couple of...
Protect Yourself: 5 Signs of a Phone Hack
Mobile threats have evolved rapidly and they're more sophisticated than ever before. Watch for these signs that you've been hacked...
Insider Threat: Former VP Goes Rogue
A former vice president of a Georgia company was recently put behind bars for wreaking havoc and sabotaging systems using bogus credentials after he was...
4 Emerging Fraud Threats
Fake faces made with AI might be the scariest. Experts are warning businesses and consumers to beware of 2021’s emerging cyber-threats. Check them out...